Managing Organizational Anxiety: A Modern Cybersecurity Story
Cybersecurity has been at the forefront of the news and top of mind for every member of the C-Suite. We are constantly asking ourselves: Am I doing everything that I should be doing? How much is enough? We see the news about breaches and threats and attacks and then doubt our preparedness. Are we being listened to? Is my activity being tracked and captured? Are devices such as cellphones, laptops, CCTV cameras, switches…compromised? From what I have been researching and hearing the answer is YES, and without pointing fingers at specific governments, companies or technologies, we should assume the worst and start from there.
We must confront the reality of “traditional” IT-level cyber threats, but also face the additional challenge of asset-level cybersecurity - or OT/IOT. This sector is managed and dealt with very differently than the traditional one. So how does someone sleep at night and feel comfortable managing their company’s level of anxiety - some might even say hysteria - and funding for cybersecurity? It feels insurmountable at times.
Traditional Landscape vs. OT/IOT Security
For now, let’s focus on the OT/IOT sector since there are many articles and recommendations addressing the Traditional scenario. Most systems in today’s buildings (HVAC, CCTV, elevators, lighting, access control, BMS, EMS…) have IP and network requirements, which can pose a cybersecurity threat. Historically, manufacturers relied on a Wide Area Network for their solutions, but the only parties privy and involved in these solutions were engineers, property managers, architects and other non-IT centric departments. On the flip side, IT departments were purposely not included in the building systems solutions - because in many cases, the Traditional safety solution would interfere with the operation of building systems. In addition, the IT department was not well-versed enough in these systems to even recommend a solution. The saying, “out of sight, out of mind” was a common message that IT adopted (as well as building operation and solution providers). It was common to just live in this ecosystem of fragmentation and uncertainty where no one knew who was responsible or liable. Unfortunately, this led to the current situation where we have billions of square feet across the world that are vulnerable with consequential risk areas. This is very overwhelming, but if you begin by setting the right level of concern and tone for undertaking the challenge, there is a lot you and your company can do.
Step One: Immediate Measures for Safety
Take a step back and look at the environment in which you are operating. What are the risks and where exactly do they reside? What is the immediate need? How mature is your organization and are you knowledgeable enough in this field to address this yourself, or do you need help? For example, is your building operating in a “Disconnected Oriented” environment? This means that if the building or systems lose connectivity to the internet (those that are connected) the building and systems will not shut down. If you are in a Disconnected Oriented environment and are in a total panic, then close all the doors until you understand the risks and vulnerabilities better. Only then can you effectively problem-solve. 
Step Two: Discovery and Identifying Goals
It’s vitally important to get educated by either joining real estate security forums or hiring a consultant to come in and audit the building(s) cybersecurity state. This could be the best thing you ever do because it will identify the areas needing improvement and where best to spend your budget. The audit usually focuses on 1) the building; 2) the technology in the building, and 3) finally the people.
Here is my example of why I wanted the audit:
For the discovery, I wanted to quantify and qualify the risks
- Unknown risks beyond what I was aware of
- I knew I needed proper networking, documentation and to assume ownership over systems
- Management awareness of the risks and need for a plan
The outcome would:
- Benchmark the risk and prioritize remediation efforts
- Build awareness within my colleagues, which prioritized the remediation efforts that were needed immediately
- Provide proper documentation/standards/policies/response plan for vendors, staff and construction team to reference
All of this would align user and business expectations; provide understanding on how to proceed; and align with management on a roadmap for a reduced risk profile for all assets. Our audit score was low but the business value was high. We understood what we can do to reduce risk and protect our buildings, and started our Asset Cybersecurity Preparedness journey.
Step Three: Planning the Road Forward
Anxiety levels were high, but we honed in on each problem to address it logically and economically. For example, we needed to implement an IDS/IDPS (Intrusion Detection Prevention System). Our building networks have either 10GB or 1GB networks. Monitoring the traffic of a 1GB or 10GB network can get expensive because there is a lot of information traveling over that connection. Imagine having to monitor a highway with three lanes or ten lanes. It does not matter how many cars are driving down the highway, but the monitoring equipment has to be able to cover a wider area - which can get very expensive. We realized that the base building systems do not consume more than 100MB, so we narrowed our solution to monitor only a subsection of the network (less highway lanes), reducing the cost but still getting the monitoring we wanted.
In addition, most IDS/IDPS out there required us to implement a standalone solution per property - also very expensive. We worked with our solution partner, leveraging a star architecture where there is one base station that communicates with a node in the asset. The node is a bridge or a transfer mechanism of the information to the base station which analyzes the traffic and logs. We rolled out the nodes in all of our properties, increasing efficiency and reducing costs.
There is a lot of talk about hardware that is not approved - or compromised by different governments. There are very specific descriptions on what it can do and the risks it  brings. These are more than rumors; to maximize safety, assume everything you hear is true. The bottom line is that if someone wants to do harm, they will find a way - but it is up to the organization to make it difficult for them - so they will leave you alone and go somewhere else. If you know that your system could be compromised by allowing remote access, then don’t expose the system to the internet. Make vendors and staff access it on premise and connect directly. Many systems that can operate without a live connection still need occasional updates.
brings. These are more than rumors; to maximize safety, assume everything you hear is true. The bottom line is that if someone wants to do harm, they will find a way - but it is up to the organization to make it difficult for them - so they will leave you alone and go somewhere else. If you know that your system could be compromised by allowing remote access, then don’t expose the system to the internet. Make vendors and staff access it on premise and connect directly. Many systems that can operate without a live connection still need occasional updates.
Understanding this (and the restrictions you implemented) allows for updating the systems in a controlled, monitored fashion - or maybe even through an external media while never exposing the system to the public WAN. Other recommendations include:
- Use government certified and approved devices for the perimeter security
- In a remote access scenario, only open doors to approved users; and even then double- and triple- authenticate them on the way in
- If you have ISP redundancy, invoke an asymmetrical network data flow

Sometimes, protecting a solution requires creativity. Perhaps the vendor did not think of the cyber aspect - or decided it would be the customers’ problem. Engineers, architects and operations will not always look for the best cyber-safe solution; they will be looking for the functionality, with cyber a less deciding factor. For example, sensors from specific brands are cheaper and easier to acquire, but could be on a banned list or are known to have a back door. In an international environment, organizations cannot always rely on a single brand, make or model. To make life more difficult, sometimes the device is not the problem - but only certain parts in the device. This is not always public information; how would you know what electronic components make up the hardware? This is why concern can sometimes become hysteria. But it is OK, because now you’ve built awareness and have a protection plan for the asset and network.
Cybersecurity as a Business Pillar
So far we’ve covered banned, stealth and unconventional or less popular methods to protect the assets and the network from OT/IOT devices. There are many other solutions a company can adopt from the Traditional sector. This includes endpoint solutions, VLANS, password policies, backups, MFA, IDS/IDPS, Zero Trust Remote access…etc. For a cyber-attack to happen, it must be introduced to the environment. Don’t only spend time and money on egress; the human factor must be considered. Someone can bring in the problem intentionally, or a device can be used to deliver a payload without the end user knowing. People download apps on cellphones. We share and connect external media to move large files, or from a private device to a work one. Is guest WiFi and/or employees’ (private use) in the office connected to the corporate network? Do you allow external media to be connected to hardware without checks and balances? The availability of web connected devices is only growing. Component costs are falling, leading to increased manufacturing and lower consumer costs. This juncture will continue to flood the marketplace with a high volume of potentially low quality IOT devices. Access to these devices has no barrier and requires no cyber or risk education. Again, there are levels of concern and various stages of effort to prevent or lower risks and potential attacks.
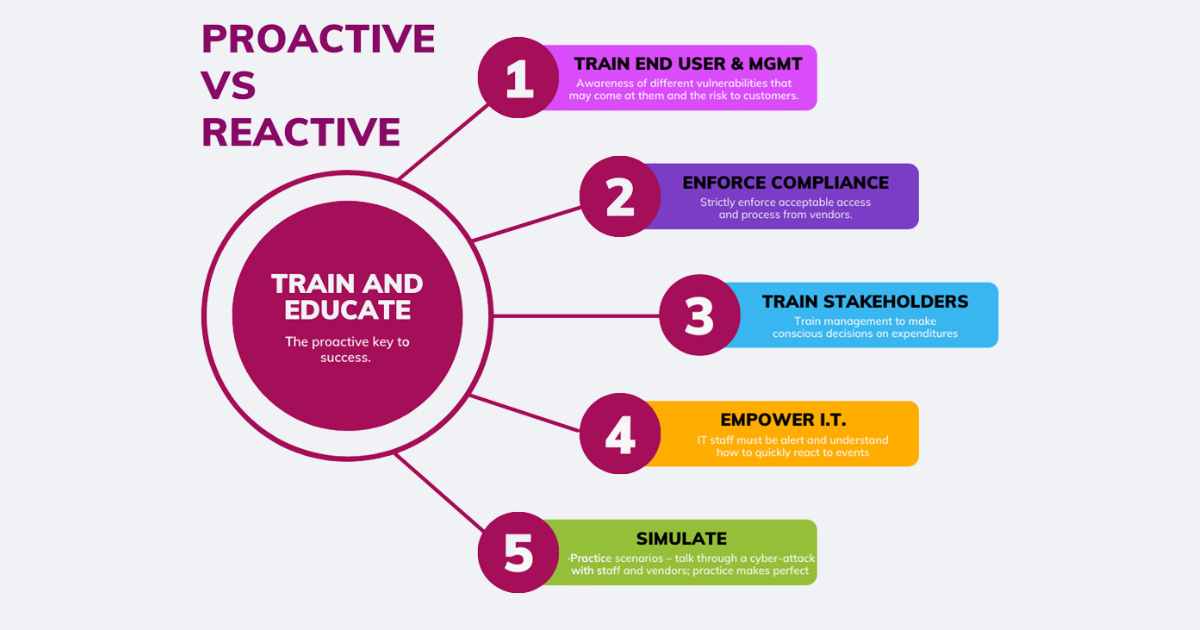
Unfortunately, today’s market is saturated with Traditional IT cybersecurity solutions and low on OT/IOT solutions. It could be because of the 90%-10% split in companies’ expenditures. In addition, it is a hard sell to prioritize projects today in a proactive vs. reactive state. Training and education is key for success.
Cyber and IT security in CRE must become a business pillar to be effective. It must lead from the top and be adopted as a way of being and operating. It should include ongoing training for all levels of staff. Training should not just be around IT operations (phishing emails, etc.) but on the OT and IOT risks that are inherently growing - and that exist in ways an average end-user might not realize.
An OT cyber watchdog program should be put in place where system users (for example, building Chief Engineer and the BMS) are trained to learn the early signs that reveal a risk or if a system is compromised. End users must be savvy enough to defend themselves vs. relying solely on IDS and IT monitoring. Cyber and risk around connected devices should be part of the conversation at every level and every move the company makes. If a company wants to purchase a device as minor as a new coffee machine, it should fall within the cyber IOT standards in place where security is evaluated.
Be aware that Cyber OT/IOT is different than Traditional IT cyber. Yes, you should be worried about ongoing threats, either happening right now in your property or sitting dormant and waiting for a date, event or person to trigger it. You and your company should be knowledgeable and understand where risks reside, what potential outcomes can be and address the topics that are relevant and within your reach (knowledge and budget). It’s everyone’s responsibility and there is a lot you can do with what you currently have - without even spending additional money. Gather your thoughts, walk the property, take notes and call your colleagues. Join some real estate cyber groups and then slowly start addressing risks. No one is asking you to boil the ocean - just focus on your specific scenario and manage your level of anxiety.
To learn more about cybersecurity for the built environment, join us at Realcomm | IBcon's annual precon event, CRE Cybersecurity Forum, on June 12 in Las Vegas. Register now!
This Week’s Sponsor
Yardi® develops and supports industry-leading investment and property management software for all types and sizes of real estate companies. Established in 1984, Yardi is based in Santa Barbara, Calif., and serves clients worldwide. For more information on how Yardi is Energized for Tomorrow, visit yardi.com.
Read Next
 5/29/2025
5/29/2025
AI Can’t Fix Bad Data. These Ideas Can Get You on the Right Track. Real estate visionaries constantly integrate innovative technology to make their organizations more efficient.
 5/22/2025
5/22/2025
Managing Building Automation and Integration Like an Investment Portfolio What if your building automation and integration decisions were managed with the same precision, discipline, and long-term vision as Warren Buffett’s investment portfolio?
 5/15/2025
5/15/2025
Tech, Talent and Transformation: 2025 Digie Finalists Announced For 27 years, Realcomm has presented the Digie Awards to acknowledge companies, real estate projects, technologies, and individuals that have advanced the commercial real estate industry through the strategic use of technology, automation, and innovation.
 5/15/2025
5/15/2025
Empowering Space Management with Data-Driven Visualization For effective CRE space management, it’s critical to centralize lease data, maximize rental square footage (RSF), improve energy efficiency and reconfigure spaces to meet changing needs.




%20(1)%20(1)%20(1).png)