Proactive Steps to Improve Building Security Using Shodan
Peter Smith, Director, Business Development, View

With the increased use of connected devices in building management, these potential access points pose a significant risk to operational technologies and it has become critical for building owners and operators to proactively identify any vulnerabilities and remediate them accordingly. Shodan is a search engine that allows users to identify and query data on Internet-connected devices. It is often used by security researchers and IT professionals to discover and analyze Internet-connected devices, including industrial control systems and other specialized equipment. Although the data Shodan collects is publicly available, bad actors can use this information to identify vulnerabilities and attack points on publicly exposed devices.
If your building has Internet-connected HVAC systems, BMS, or other devices, you need to take steps to secure building networks and protect your tenants from hackers. For example, if a BMS is not properly secured, an attacker can gain access to it and manipulate temperature set points in the building, affecting working conditions and productivity. Although this type of attack might at first seem trivial, it can result in serious consequences in certain scenarios, such as for data center operations or the storage of perishable inventory.
Attackers often exploit one “weakest link” system with the goal of accessing a different connected system. For example, if an account owner uses the same credentials to log in to both the BMS and a company database, attackers could obtain login information from a compromised BMS device and then use it to access confidential company data. A notorious example is the 2013 Target attack where hackers were able to infiltrate the company’s network using credentials obtained from a compromised HVAC system. The data breach exposed approximately $40 million credit and debit card accounts and cost the company an $18.5 million settlement and $202 million in overall recovery costs.
These types of attacks can result in damage and production issues that add up to significant losses. However, in addition to the direct financial costs of these attacks, there are also reputational implications for the building owner or operator, leading to a loss of trust from customers, tenants, or other stakeholders.
The best remediation for these scenarios is a zero-trust architecture in which all systems are locked down and inaccessible to the Internet and require validation at every access point. By taking proactive measures to identify vulnerabilities and secure operational technologies, building owners and operators can reduce the risk of costly and reputation-damaging attacks.
Using Shodan for security insights. It is important to regularly use tools like Shodan to help identify any building devices that are publicly exposed. You can sign up for a free Shodan account and run simple queries on their global index. Here are some ideas as a starting point for your search:
- Company name
- Building names and addresses
- Manufacturer of your BMS
- Names of smart building applications that run on-premises
- Vendors that provide hardware and sensors
For example, on the Shodan dashboard we searched for a common BMS provider. The resulting reports show device data including geographic location, network ports, organization names, specific product models, and much more.

To quickly filter the results, you can select a data point from the left menu, such as country or product. If you want to dig deeper, you can run more intricate queries, configure notifications, and even integrate with the Shodan API.
We selected one of the devices and can see some location details, hostname, company information, and even a Remote Desktop login screen.

What should you do if you find one of your devices in Shodan? Any connected device that is publicly exposed is a potential vulnerability and compromises a zero-trust architecture. To mitigate this risk, implement a proactive yet simple security solution such as View Secure Edge that centrally manages your building devices and networks. With our help, one of our clients identified seven properties with exposed devices (public IP addresses and remote desktop session feeds) and through the installation of Secure Edge was able to remove them from the public Shodan directory.
This Week’s Sponsor
View is a Silicon Valley-based technology company with the mission to transform buildings into responsive environments. We have built the only complete, cloud-native platform to deliver on the promise of smart buildings. Smart Building Cloud transforms buildings into healthy and sustainable environments while increasing cybersecurity and efficiency for building owners and their tenants. Find out more at www.smartbuildingcloud.view.com.
Read Next
 3/27/2025
3/27/2025
The Convergence of Edge Computing, Cloud, and AI in Building Automation and Smart Buildings In the built environment, we have seen the convergence of Operational Technology (OT) and Information Technology (IT), later expanding to include Workplace Technologies (WP).
 3/27/2025
3/27/2025
DC Power: A Holistic Approach to Energy Savings in Commercial Buildings In today's energy-conscious world, businesses constantly seek ways to reduce their carbon footprint and operational costs.
 3/13/2025
3/13/2025
How to Achieve Eco-Friendly Facility Management Commercial real estate operators and facility managers are focusing on sustainable practices to minimize environmental impact, create healthier workplaces, improve productivity and lower operational costs.
 1/23/2025
1/23/2025
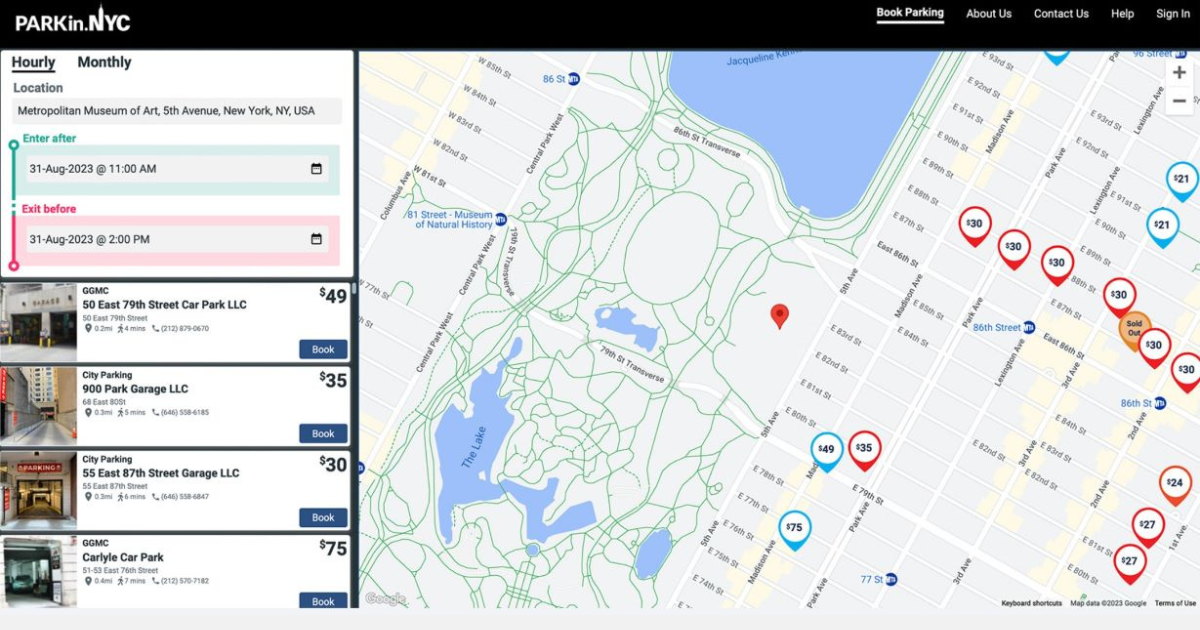
When It Comes To Managing Properties’ Parking, Technology Is Key It’s easy for developers and real estate owners to think of parking as a necessary evil. They know they have to provide it (often, because it’s mandated by code), they understand that prospective tenants and buyers expect to be provided parking, but they haven’t figured out how to maximize its value.


.gif)